CyberPatriots, Digital Footprints, Data Backups, and AFA Cyber Patriot Camps
Topics Covered
- Guest Speaker: Rachel Zimmerman, Rebecca Dalton, and Frank Zabrowski
- CyberBytes: Digital Footprints
- Technology Corner: E-mate Backups
- Cyber Opportunities: AFA CyberCamps
Aired: March 16, 2021
About this Show
Guest Speakers:
Rachel Zimmerman is the Director of Business Operations and Deputy Commissioner for CyberPatriot as she oversees the AFA CyberCamp program, the Elementary School Cyber Education Initiative, and the Cyber Education Literature series. Rachel was also one of the 15 awarded with the 2020 Mission Award by Homeland Security.
Rebbecca Dalton who is the Director of CyberPatriot Engagement & Outreach, she was a pillar in the transition to the virtual National Finals and she has worked with King Saud University in Saudi Arabia to conduct a cybersecurity workshop. Rebecca is also very graphically talented as she has designed CyberPatriot merch such as this one
Frank Zaborowski who is the Senior Director of Competition Operations for CyberPatriot as he plans, coordinates, and executes the National High School Cyber Defense Competition for about 4801 teams of high school and middle school students.
Cyber Bytes: Digital Footprint
Your digital footprint is a trail of all of the data that you leave online. It’s like little cookie crumbs or footprints left in sand that could lead someone to you. You increase your digital footprint every time that you send an email, make a post on social media, or visit a website online. Digital footprints can be broken down into two different types: active and passive.
An active digital footprint is easier to understand since this is the information that we are putting out ourselves. This includes every post, tweet,snap, email, text, like, or comment you make. Someone who has a high snapchat score, regularly makes posts on a blog, posts a lot of images on their instagram are going to have a larger digital footprint than someone who spends a lot of time off the internet. In this past year all of our digital footprints have greatly increased with COVID and the pandemic. Having school and work be online we have all increased our active digital footprints by the work that we have put out.
A passive digital footprint is the data that is collected from you while online. Any data that is collected from you without you actively sharing it is your passive digital footprint. A website typically will save your IP address to a web server every time you login to that website to track the users that are coming to their website. Another form of increasing your passive digital footprint is when web browsers save your search history.
A great way to look at both active and passive digital footprint is through the use of cookies. Cookies are little files that are on a website in order to help store information as well as track user activity. An example of when cookies are used actively is when you allow a website to store your username, password, and personal information. Cookies also work passively by collecting information about what you’re viewing in order to tailor ads to you later.
Having a digital footprint is not something that people should be worried about. Everyone who has ever used the internet has a digital footprint. It’s what your digital footprint says about you that people should be monitoring. Whenever you put something online there is no guarantee that it will be able to be erased or taken down at some point. You may delete a picture or post that you make online, but these could be stored in a company’s web server or saved in a screenshot. Making sure that you have a good digital footprint is really important because employers look up someone’s digital footprint before hiring them. In some cases people have gotten fired for what they have put out on the internet. Before you post something, think about all of the different people that could end up seeing that photo and consider if it is something that you would want them to see. One way to view your digital footprint is to Google yourself and see what pops up. This way you can see what is about you on the internet and can possibly get some of this information taken down. Use nicknames while online and don’t publicly share any personal information about yourself. Just remember that when you’re using the internet that you want it to be a reflection of yourself that you would like everyone to see
Technology Corner – Backups
Follow the Backup E-mate: https://mirrorlearning.org/emate2/backups/pub/backups/Assets/index.html
Today’s E-Mates demonstration lab will be about backups! Backups are a critical part of security, as they allow users to restore lost or corrupted data back to its original form.
Page 1: Some examples of devices that need to be backed up are servers, workstations, laptops, tablets, smartphones, or virtual machines.
Page 3: Item-level backups
Item-level backups include collections of information that are items. An example is backing up the files in a file system. Objects can be stored in storage systems like Amazon S3, Azure Blob, or Google Cloud storage.
The frequency of backups is also important. For example, backups can be scheduled daily, weekly, monthly, or continuously. This is a safety mechanism in case files are lost or corrupted, as I mentioned before. Even though data storage requirements can be difficult to manage, there are many storage options, such as external media (hard drives, floppy disks, etc.) or cloud databases.
Page 4: Archive Bit
The archive bit is a file attribute. Various backup utilities use the archive bit to determine which files to back up and which files to skip. The archive bit turns on when a user creates and saves a new file or modifies an existing file.
As you can see in the demo, there are files with a letter A to indicate that they have an archive bit. This tells the backup utility to backup those particular files.
Page 5: Full Backup
A full backup basically is what the name indicates. It creates a full copy of the entire data set. This is usually periodic because it takes more time and storage to complete. This process also uses the most network and server resources.
Page 6: Incremental Backup
Incremental backups require less time to complete daily and can be used simultaneously with a full backup schedule.
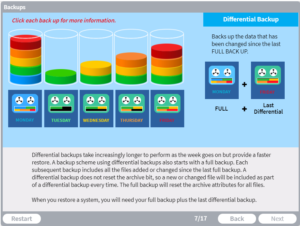
Page 7: Differential Backup
Differential backups take increasingly longer to perform but provide faster restore.
Page 8/9: Compare Backup Types
- The diagram shows the different backup strategies (full, incremental, differential) and the progression of each type of backup
- This chart compares the data backed up, backup time, restore time, and storage space for each type of backup.
Cyber Opportunities: AFA CyberCamps (CyberPatriot)
As we near the end of second semester, summer opportunities are just around the corner. The AFA CyberCamps are cyber camps hosted by CyberPatriot each summer. Normally they’d be held in person, but this year, CyberPatriot has modified the camp materials so that camp can be held online to keep us COVID-safe. There’s two different levels—beginners and advanced.
The schedule of the beginner camp is laid out like this. On Day 1, students will be given a general introduction of cyber, including the CyberPatriot competition and different cyber careers and their merits. From then on, they’ll be introduced to the two main operating systems for the CyberPatriot competition, which are Windows and Linux. Throughout the next three days, students will be able to develop checklists and learn the basics of those OS’s. And on the last day, they’ll put their new knowledge to use and compete against each other in a CyberPatriot-like competition setting, with two images.
If you’re interested in the advanced camp, the curriculum is definitely more comprehensive, and you’ll be introduced to Cisco as well. The last day is also a competition, with more difficult Windows and Ubuntu images.
Unfortunately, you won’t be able to sign up as an individual student through the website. You’ll need to find a host near you, whether it’s a program at your school or talking to one of your teachers about it.

