Chappell University, Microsoft Exchange Hack, Wireshark, PicoCTF, and RUSecure CTF
Topics Covered
- Guest Speaker: Laura Chappell
- CyberBytes: Microsoft Exchange Hack
- Technology Corner: Wireshark
- Cyber Opportunities: Capture The Flag Opportunities
Aired: March 16, 2021
About this Show
Guest Speaker:
Laura Chappell, Founder of Protocol Analysis Institute, Inc., Chappell University, and Wireshark University Laura is a researcher, educator, and author. Best known for founding Chappell University, Wireshark University, and the WCNA Certification program. Laura has authored books on Wireshark. LinkedIn Profile: https://www.linkedin.com/in/chappelllaura

Cyber Bytes: Microsoft Exchange Hack
Relevant Terms
- Microsoft Exchange Server: an email server that works with web-based mail clients (such as Microsoft Outlook) that connects and manages emails and calendars
- HAFNIUM: a Chinese hacking group that primarily targets United States entities across different types of industry sectors
- Zero-Day Exploit: an unknown exploit in the wild that exposes vulnerabilities in software and/or hardware that cause problems before detection; when attackers release malware before a patch from the developer was created to fix the vulnerability
- On-premises: hackers targeted the software that is installed and runs on computers on the premises of the Exchange Server, as opposed to a remote facility like a server farm or cloud
- In the Wild: technologies or software products that have completed development and become a publicly used tool, are no longer under control of their makers; when a virus is “in the wild” it spreads as a result of normal everyday operations between ordinary, unsuspecting users
- Web Shell: a malicious service that enables remote access and control to a web server by allowing attackers to run commands on the servers
What Happened? On March 2nd, Microsoft announced that threat actor Hafnium launched multiple zero-day exploits to attack their Microsoft Exchange Server. The attackers exploited vulnerabilities in the wild to access on-premises Exchange servers, allowing them to steal emails, download data, and install additional malware to gain long-term access to their victims’ servers. The attacks were first detected but not publicly disclosed in January 2021 through Volexity and FireEye. Volexity, a security monitoring service provider, discovered anomalous activity from a couple of its customers’ Microsoft Exchange servers when it identified that a large amount of data was being sent to IP addresses that were not tied to legitimate users. FireEye’s Mandiant Managed Defense observed activity within the Exchanger Server’s client environment that included the creation of web shells for access and remote code execution. Since then, the Exchange Server hack has infected tens of thousands of government offices, businesses, and schools within the U.S. The hack has impacted at least 60,000 Microsoft customers worldwide.
What Did Hafnium Do? Hafnium compromised tens and thousands of Exchange servers by gaining access with either stolen passwords or exploiting vulnerabilities to disguise themselves as users who should have access. Once gaining access to the server, Hafnium created a web shell to control the compromised server remotely. This software then allows the malicious actors to enter in administrative commands through a terminal window in order to steal data from an organization’s network and lead to further compromise. The vulnerabilities that have been exploited were CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. You can read more about the technical details of each vulnerability on Microsoft’s security blog here: https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/. Hafnium was also able to download Exchange’s offline address book from affected systems, which is a copy of an address list that can be accessed while disconnected from the server, containing information about the organization and their users. While most attacks are located within the United States, organizations in other parts of the world, particularly Germany, have been targeted as well.
Response Microsoft released patches to address their e-mail server vulnerabilities on March 2nd, meaning that the attackers were within their servers for nearly two months. The president of Volexity has stated that “if you’re running Exchange and you haven’t patched this yet, there’s a very high chance that your organization is already compromised”. Chris Krebs, former head of the Cybersecurity and Infrastructure Security Agency warned organizations that they should “assume compromise” of on-premises servers and act accordingly. Because nearly all organizations use email, and Microsoft Exchange is widely used, this attack is very worrisome. While Microsoft did issue patches, they do not help disinfect systems that have been already compromised. The webshells will continue on until it is actively removed. Microsoft has strongly recommended its customers to upgrade their on-premises Exchange environments to the latest supported version and for organizations to investigate their servers to ensure that they have not been compromised. Microsoft has also provided alternative mitigation techniques to help customers who need more time to patch their systems.
Technology Corner – Wireshark
Use this video if you need to install Wireshark 🙂
What is Wireshark? Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Mainly used for Network Analysis, where experts can listen to and analyze network traffic, using the data to troubleshoot many things, such as faulty network devices, software misconfigurations, delays in services, packet loss, and many more. So to understand Wireshark a little easier, I have provided a scenario with a telnet capture but, first for a little bit of context I would like to talk about the OSI model, for it is extremely important when looking at Wireshark.
OSI Model So a lot of things happen when two things are communicating, in other words there are a lot of moving parts that are happening when you access a website or are trying to communicate with another device. We can explain this complicated process with the OSI model. The OSI stands for Open Systems Interconnection, and is a reference model. Note the key word REFERENCE model, so that means it is something that we look to if we need further information, it is not the actual protocol that is being used, which is the TCP/IP protocol suite, which I will talk about later.
Here are the layers simplified:
Application: The application that will be initiating the communication, in other words network aware.
Presentation: Formats the data (HTML, JPG, MP3)
Session: Stops. Starts, and maintenance of session
Transport: TCP vs UDP (Reliable vs unreliable) and ports
Network: Generic, logical addressing, in other words IP addresses
Data Link Layer: MAC addresses, physical addresses
Physical: Turns data into 1s and 0s
The way I remember it is Please Do Not Teach Students Pointless Acronyms. Funny right? Cause you’re using an Acronym o_0
Here is a really cool explanation of the OSI model using a scenario of when you would order pizza, not the best explanation but, should get you thinking.
TCP/IP Protocol Suite So that brings us to the TCP/IP protocol suite, which is actually used in computer networks and refers to the suite of data communication protocols. Protocols is just another word for a rule, if you want all the devices to communicate with each other you need to be following the same rules right? The TCP/IP protocol suite was developed by the Department of Defense, It is named from two of the most important protocols in it: the Transmission Control Protocol (TCP) and the Internet Protocol (IP), which were the first two networking protocols defined in this standard. Here is more history on the protocol suite.
What’s the difference? So besides the fact that they have different amount of layers, the main difference between the two is that the OSI model is a reference, meaning we mainly use it when we’re troubleshooting and we’re looking for someone to blame because, it has more layers and it is easier to narrow down the problem. The TCP/IP protocol suite was created so we actually have protocols, or rules, to follow when we communicate across the network so that the thing actually doing the work (the computer) can understand it and execute communications.
Why do we need layers? The main reason why we have these reference models and protocol suites is because, communication is a big process, that the way to break down the process is by putting it in layers. We do these with protocols, which again are a set of rules, which allow us to communicate so that every device can understand.
Putting it into practice! Alright so here I have a packet snipped from Wireshark that shows some of the layers that you have seen. Lets see if you can figure out which each part means. 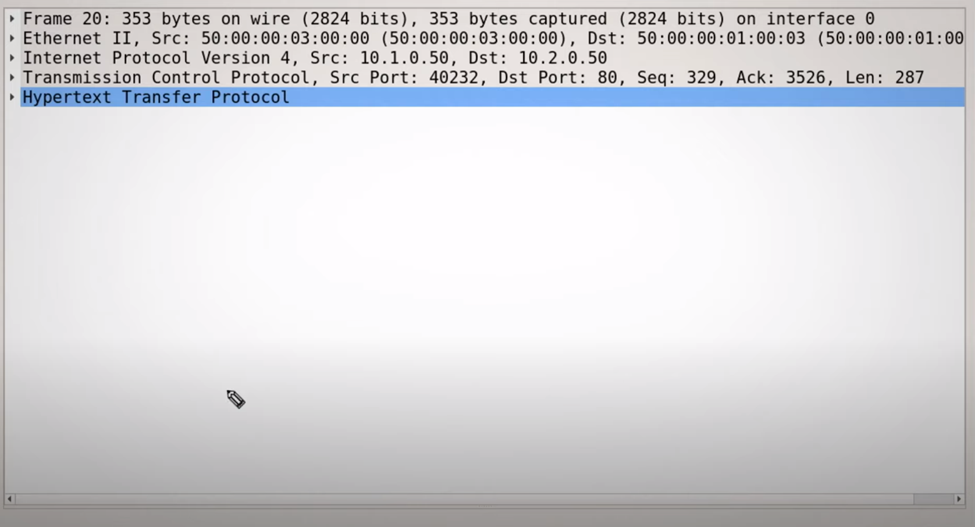
That’s one of the big things about Wireshark, being able to pull out traffic and understand it. Here is a link to a pcap file that you can open in Wireshark and try to understand. I just wanted to show you one more thing that can be useful, which is following a telnet session and finding the password for a device. (If you do not know what telnet is you should watch my segment here)
- Open the pcap file!
- Filter for tcp
- Right click on one of the packets
- Hover over follow and click tcp stream
And BAM! You have just discovered sensitive information about a cisco device. Congrats! If you want more practice there are many resources on YouTube you can try out, such as Laura Chambell’s YouTube channel where she teaches some topics that are related to even more things. Hope it helps!
Cyber Opportunities: picoCTF & RUSecure CTF
This week we are going to talk about the PicoCTF which is a capture the flag cyber competition. Middle schoolers and high schoolers can compete, just have to be 13 years and older. Competitors must reverse-engineer, decrypt, hack, break, etc. to complete the challenges and gain the flags. They started registering in February and the competition period is from March16th to March 30th. The teams can either be a single person or up to 4 people. The winners are announced in April. The prizes that are given are if you place 1st then you get 5,000 dollars and a paid trip to Carnegie Mellon University, second place gets 3,500 dollars and a paid trip to CMU, 3rd place gets 2,000 dollars and a paid trip to CMU. The highest scoring all middle-school gets 750 dollars and the second highest scoring all middle-school team gets 500 dollars. More information can be found on their website which is sent in the chat. Another opportunity is the Radford University CTF also known as the RUSecure CTF. It is another capture the flag competition which is open till noon on March 26th. Anyone can compete up till public or private college students. The teams must consist of one coach and minimum of 3 players, you can have up to 5 competitors. You solve the challenges and earn the flags. It is a free competition. More information can be found on their website which is sent in the chat. That is all there was in the opportunities section.



